...
| Expand |
|---|
...
|
...
|
...
|
...
|
...
|
...
|
...
|
...
|
...
|
...
|
...
|
...
|
...
|
...
|
...
|
For a cloud-based content management and distribution network, database security and server reliability are of the highest priority. The BrightSign Network (BSN) has been built with these principles in mind. This section provides a general overview of security and recovery architecture for BSN. Note that some specific information may be withheld for security purposes.
Physical Security
All BSN servers are hosted using Amazon Web Services (AWS). Amazon strictly controls physical access to its platform infrastructure using military-grade perimeter control, as well as state-of-the art surveillance and intrusion-detection systems.
...
Physical assets used by BrightSign employees are managed and classified by the VP of finance. Relevant asset changes are communicated to appropriate constituents on a regular basis.
Virtual Data Center Security
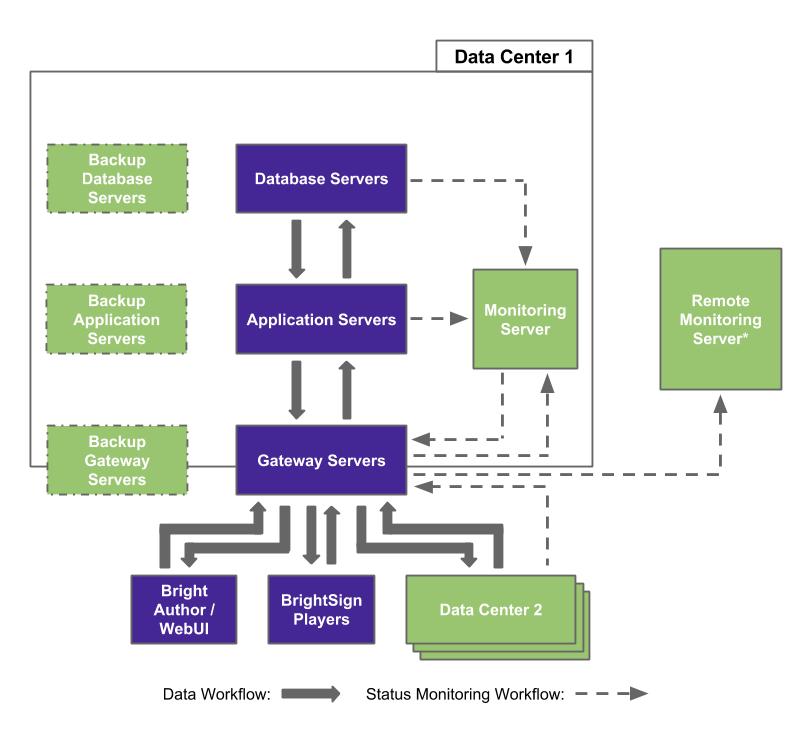
All communication with BSN is mediated by two pairs of gateway servers. All calls to BSN domains are directed to these gateways. Each gateway communicates with a specific set of BSN nodes, and each pair of gateways is assigned traffic from a geographically distinct part of the globe.
Nodes located within the security group (i.e. behind the gateways) can communicate directly with each other because they have a list of internal IP addresses; however, these addresses are not communicated outside of the security group.
DDoS Protection
The gateway servers protect internal nodes from being overloaded in case of a distributed denial of service (DDoS) attack. Furthermore, there are backup gateway servers that are running “warm” 24 hours a day and can immediately come online if one or more gateway becomes overloaded with connections.
Each gateway also has process code for the other gateways installed on it, so all gateways can be rotated to different routings or geographical assignments in event of an attack.
General Disaster Recovery
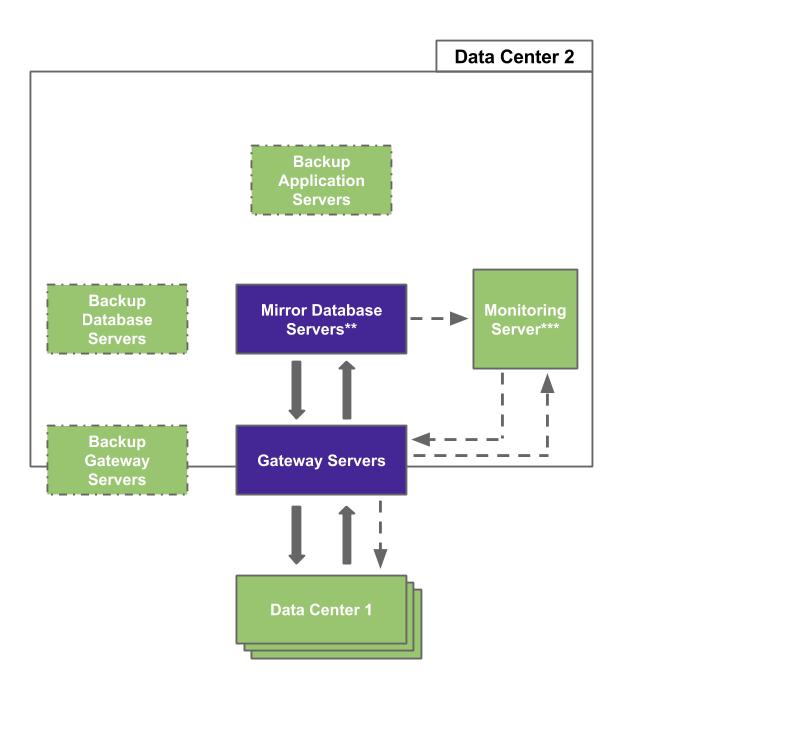
Each BSN server node has a backup server that can take over in case of unscheduled downtime. The database server for the BSN has both a mirror and a backup that frequently update to prevent data loss in event the production database goes offline.
...
Business continuity and disaster recovery (BCDR) tests are conducted quarterly. Additionally, a Business Impact Analysis is conducted annually: All server instances are turned on and off to test resilience of the system to outages.
Protection Against Intrusion Attacks
Quarterly scans are carried out to check for hacking and intrusion attempts. White-hat contractors are also employed to attempt breaching public-facing web applications. All server operating systems are also protected with industry-standard virus detection software.
...
SQL queries against the database are used to retrieve/copy data without affecting the metadata.
Administrative Security
Information Assets
All BSN and BSNEE software repositories and related confidential material are managed by relevant subject matter experts within the company. There is no broad-based access to this information within the company.
...
The full BrightSign privacy policy can be viewed here. Management reviews all code and configuration changes to ensure that they are in compliance with the privacy policy.
...
BSN is not HIPAA compliant and should not be used to store or transmit medical information.
Application and Communications Security
The BrightSign Network interacts with digital signage environments by communicating with BrightSign devices, BrightAuthor software, and the BSN API (i.e. the browser-based BSN WebUI).
Devices
The BrightSign Network and BrightSign devices communicate with each other using HTTPS, rather than HTTP. BSN requires a device to authenticate itself with a hashed and salted phrase before it can download content.
| Note | |
|---|---|
| title | NoteBecause of interference with caching/proxy servers, the file download service uses HTTP, but media files can be optionally encrypted using AES-128 |
BrightAuthor
BrightAuthor requires BSN account authentication before affecting changes on the BSN servers. All communication between BrightAuthor and the BrightSign Network is carried out using HTTP and HTTPS depending on specific function. Tokens are used in all HTTP communication.
BSN API
Every API call requires account authentication before affecting changes on the BSN servers or returning content from the database.
Data Center Operation Block Diagrams
...
Notes
* During normal operations, the Remote Monitoring Server only receives updates from the Monitoring Server within Data Center 1. If the Remote Monitoring Server is no longer receiving updates from the Monitoring Server, it will switch to receiving information directly from each Gateway, Application, and Database node.
** The Database Servers in Data Center 2 constantly mirror the Database Servers in Data Center 1.
*** The Monitoring Server in Data Center 2 reports to the Monitoring Server in Data Center 1.